Recently the Apps on demand was released, essentially this an Azure market place offering from VMware aka Broadcom. You can deploy App Volumes manager virtual machine that runs Windows Server 2022 with App Volumes Manager pre-installed. Additionally, deploy Azure file share and database configuration.
What is an AppStack
An AppStack in VMware App Volumes is a virtual container that contains a set of applications packaged together. It’s used in virtual desktop environments such as (AVD and Windows 365) to dynamically deliver these applications to users. AppStacks are read-only, can be attached to user sessions transparently, and appear as if the applications are natively installed. They offer efficient application management, allowing for easy updates and maintenance without impacting the underlying system. This approach simplifies application lifecycle management and enhances user experience in virtualized desktop scenarios.
Prerequisites
You’ll need the following things ready before you can rollout App Volumes:
- Azure Subscription: Have an active Microsoft Azure subscription. Azure Documentation
- Azure Permissions: Ensure permissions to create virtual machines for App Volumes Manager, storage accounts, and file shares on Azure.
- Access to On-Prem Active Directory: Required for identity and access control.
- Azure Virtual Desktop Access: For remote connectivity.
- Azure AD Connect: Install Azure AD Connect on the Active Directory Domain Controller.
- Active Directory Configurations:
- On-premises Active Directory Server connected through VPN or Microsoft Azure ExpressRoute. Microsoft Azure ExpressRoute Documentation
- Active Directory Server located in Microsoft Azure. Active Directory on Azure-Provisioned VM
- Note: Microsoft Entra ID (Azure Active Directory) is not supported.
- App Volumes License File: Download and install the App Volumes license file. App Volumes in Azure follows a Bring Your Own License model. VMware App Volumes Product Download Page
- Download App Volumes Agent:
- Visit VMware Customer Connect
- Navigate to Downloads > VMware App Volumes > Download Product.
- System Requirements Awareness: Familiarize yourself with the system requirements for using App Volumes. VMware App Volumes 4 Installation Guide
- SQL Server Database for Production: For a production environment, ensure the availability of an existing SQL server database, as the default SQL Server Express Database is not recommended for production use.
My party came crashing on the requirement of Active Directory (AD) Domain Controller. In my entire Azure, Azure Virtual Desktop, Windows 365 Cloud PC and Microsoft Intune I have made deliberate choice to keep it with mordern management\authentication and follow the Microsoft best practice guidance. Though I am not able to complete the entire configurations due to AD I decided to share whatever configurations I manage to perform to deploy the AV Manager appliance within my Azure subscription for this blog post.
Starting in the Azure Portal
- Access the Marketplace: Begin by navigating to the Microsoft Azure portal and clicking on ‘Marketplace’.

- Find VMware App Volumes: Search for the ‘VMware App Volumes’ offer and click on it.
- Select App Volumes Version: In the VMware App Volumes Azure Application page, choose the desired version from the Plan drop-down box.
- Click ‘Create’

Deploy the Virtual Machine Appliance
- Details: Select your Subscription and Resource group. You can also create a new resource group if needed.
- Instance Details: Choose the Region and enter the name for your virtual machine. Set up the credentials for the local administrator. (#TIP – Ensure you deploy the Appliance where the session host pools are located)
- Public IP Address: A new public IP address is created by default, but you can opt for an existing one or none at all. (#TIP – This allows accessing the App Volumes Manager over the internet )
- DNS Prefix: If using a public IP address, consider creating a DNS prefix for easier access. (#TIP – Pick a friendly name I decided to leave it as defaults)
- By default, a new virtual network and subnet are created. However, in my situation, I want to leverage the existing VNET and Subnet.

- Database Selection: Choose between a Local SQL Server Express Database (not recommended for production) or a Remote SQL Server database. Enter the necessary database connection details. (#TIP – Explore for production use evaluate using the Azure SQL DB as its a managed SQL instance and you will not have the overhead of managing and maintaining a SQL Server)
- File Share Configuration: Decide if you want Azure Marketplace to automatically provision storage with file shares or use existing storage. Configure accordingly. (#TIP – Same if you have Azure Dell or NetApp Files storage you can leverage that or using Azure storage account)

- Tags: Add any desired tags. (#TIP – Ensure you add the tags as it will help you later during Billing and Automation)
- Review and Launch Deployment: Review your setting Click ‘Create’ to start the deployment process.

- Navigate to App Volumes Manager Admin UI: This is where you’ll configure Active Directory and other settings.
- Configure Storage: If you opted out of automatic storage provisioning, manually configure the storage in the App Volumes Manager admin UI.
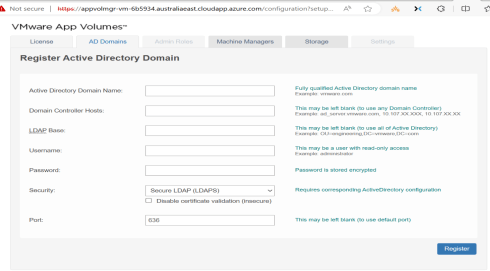
- When you navigate to the Storage the newly created SMB shares are listed for templates and AppStacks stroage.

I will come back to this blog post once I learn more about the “No AD” mode as this will enable me to further integrate App Volumes into my Azure Virtual Desktop and Windows 365 Cloud PCs.
Resources deployed within the Azure Resource Group
Following resources are deployed within your Azure Resource Group for App Volumes

Whislist
I would like to see the following enhacements at a later day:
- VMware aka Broadcom should evlaute a complete SaaS offering taking it to the next level instead of deploying an appliance and required to do alot of configuration. Just give me “as a Service” and the only responsiblity is to create/update and mange the applications with Entra ID Groups.
- Microsoft Entra ID integration is a must
I hope you will find this helpful information for getting started with App Volumes for Windows 365 Cloud PC and Azure Virtual Desktop. Please let me know if I have missed any steps or details, and I will be happy to update the post.
Thanks,
Aresh Sarkari


































































































Recent Comments